Reconnaissance in PenTesting: A Beginner’s Guide

Where ethical hacking or penetration testing is concerned, the initial phase is probably most critical and most neglected by novices. It is known as reconnaissance, or simply as recon.
Consider recon as the information collection phase. As a burglar might plan to break into a house examining windows, doors, alarms, or the owner's schedule so a penetration tester collects as much information as they can about a target before conducting any active attacks.
In this blog, we will dissect the reconnaissance phase into bite-sized pieces that you'll understand, discuss tools you can utilize, and provide real-world scenarios to make the idea concrete.
Prefer watching instead of reading? Here’s a quick video guide
What is Reconnaissance?
Reconnaissance is the attack preparatory phase where a tester gathers information on a target to find possible vulnerabilities. It is no direct damage or attacks merely data gathering and analysis.
There are two primary forms of reconnaissance:
- Passive Reconnaissance – Information gathering without directly contacting the target.
- Active Reconnaissance – Engaging the target directly to gather information, e.g., port scanning or service scans.
Passive Recon: No Touch, No Trace
Passive recon is all about collecting information in a covert manner. As you're not touching the target system directly, you're less likely to be seen. Here's what you can do:
WHOIS Lookup
Employ tools such as whois.domaintools.com or Linux's whois command to obtain:
- Registrant name of the domain
- Registrar details
- Contact emails
- Name servers
- Creation/expiration date of the domain
This can provide hints regarding the organization, admins, or possibly internal setup.
DNS Enumeration
Utilize tools such as dig, nslookup, or dnsdumpster.com to:
- Identify subdomains
- Retrieve DNS records such as MX (mail), TXT, and A (IP address)
- Uncover concealed web portals or services
Google Dorking
Google is not only a search engine it's an information treasure trove. Utilize special searches such as:
site:openexploit.in intitle:"index of"
site:openexploit.in filetype:pdfThese dorks have the capability to reveal sensitive directories, documents, and configuration files.
Social Media & Employee Details
Platforms such as LinkedIn, Twitter, or Facebook have the ability to reveal:
- Employee names
- Job titles (such as "System Admin")
- Technology stack
- Internal naming conventions
- Email formats (for example, [email protected])
This assists in social engineering or designing phishing attacks later.
Active Reconnaissance: Knocking on the Door
After passive recon provides you with a picture, active recon assists you in probing further but this means direct interaction, which can be detected.
Port Scanning
Tools such as Nmap can scan open ports and services:
nmap -sS -Pn -T4 openexploit.inYou may find:
- Open ports (such as 22 for SSH, 80 for HTTP)
- Running services (e.g., Apache, MySQL)
- OS fingerprints
This assists you in discovering attack surfaces such as outdated software or poorly configured ports.
Service Enumeration
Utilize tools such as Nmap scripts, enum4linux, or Nikto to:
- Discover software versions
- Verify default credentials
- Expose directory listings or vulnerable plugins
Example:
nmap -sV --script vuln openexploit.inSubdomain Enumeration
Utilize tools such as:
- Sublist3r
- Assetfinder
- Amass
The discovery of hidden subdomains such as dev.openexploit.in or staging.openexploit.in can reveal weak entry points.
Tools You Should Know
The following are some commonly used recon tools with a brief description:
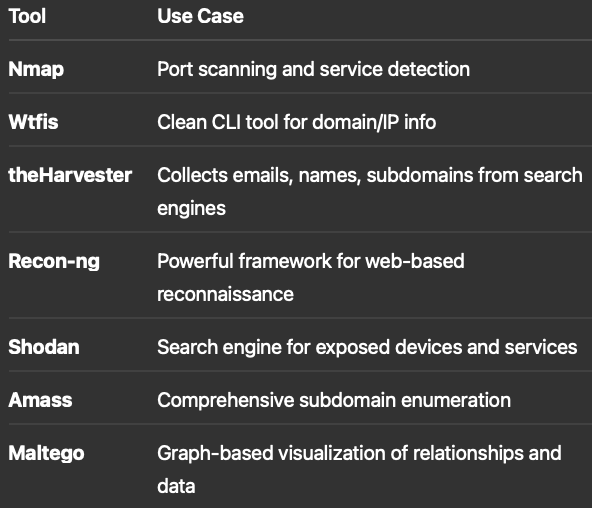
Example Recon
Suppose your target is openexploit.in. Here is a simplified recon workflow:
- WHOIS Lookup – Gather registrar info and admin emails.
- DNS & Subdomain Scan – Utilize Amass and dnsdumpster to discover subdomains such as dev.examplecorp.com.
- Google Dorking – Search site:examplecorp.com filetype:pdf for internal documents.
- Shodan Search – Search IPs examplecorp.com uses to determine exposed ports.
- Nmap Scan – Scan open ports on IPs of primary importance.
- Service Enumeration – Utilize Nmap scripts or Nikto to locate possible vulnerabilities.
- Social Media Mining – Search LinkedIn for employee names such as "John Doe – Network Engineer."
You haven't launched anything yet but you now have open ports, running software, employee information, and probable attack vectors.
Why Recon is Important
Skimping on recon is like attempting to pick a lock blindfolded. Here's why it's important:
- Reduces noise: You don't target every door only the vulnerable ones.
- Saves time: You target only probable vulnerabilities.
- Increases stealth: With sufficient passive recon, you may not require noisy scans.
- Enhances precision: You don't guess by creating an actual-world map of the target.
Legalities and Ethics
Have permission first before carrying out recon. Unauthorised recon even passive on live systems may be illegal under cyber security legislations such as the Computer Fraud and Abuse Act (CFAA) or India's IT Act.
Limit yourself to bug bounty programs, test environments such as TryHackMe/Hack The Box, or internal sanctioned engagements.
Last Words
Recon is where great pentesters turn excellent. The better you recon, the wiser your attacks and the greater value you provide to clients or businesses.
Before you begin bashing doors and taking advantage of services, breathe. Act like a detective, not a battering ram.
If you're studying penetration testing, make reconnaissance your buddy. Because in cyber war, knowledge isn't simply power it's the first blow.




