FreeBSD RCE: ND6 Router Advertisements Exploit
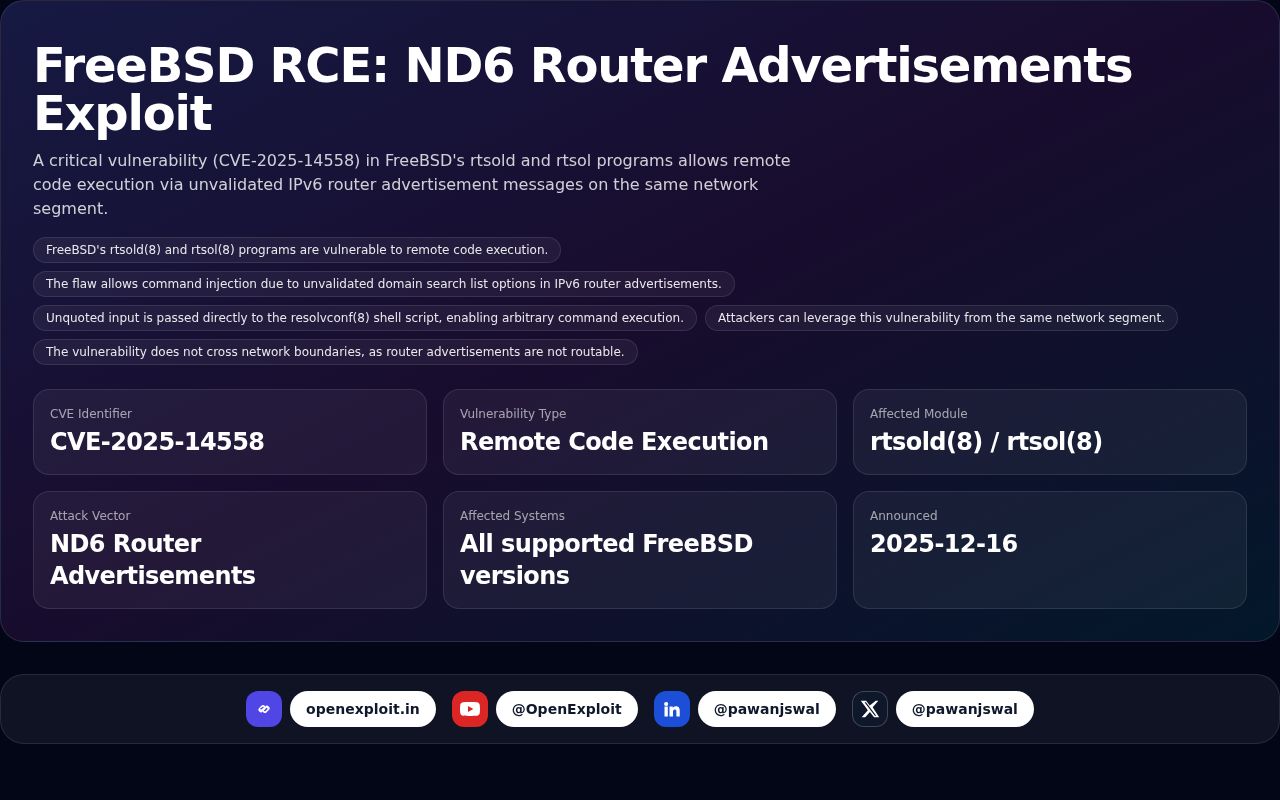
A critical vulnerability (CVE-2025-14558) in FreeBSD's rtsold and rtsol programs allows remote code execution via unvalidated IPv6 router advertisement messages on the same network segment.
A critical flaw in FreeBSD's rtsold/rtsol opens the door to remote code execution. Is your IPv6 network segment secure? Immediate action is required to prevent compromise.
A critical vulnerability (CVE-2025-14558) in FreeBSD's rtsold and rtsol programs allows remote code execution via unvalidated IPv6 router advertisement messages on the same network segment.
Source: The FreeBSD Project — Source link
Highlights
| Metric | Value | Notes |
|---|---|---|
| CVE Identifier | CVE-2025-14558 | |
| Vulnerability Type | Remote Code Execution | |
| Affected Module | rtsold(8) / rtsol(8) | |
| Attack Vector | ND6 Router Advertisements | |
| Affected Systems | All supported FreeBSD versions | |
| Announced | 2025-12-16 |
Key points
- FreeBSD's rtsold(8) and rtsol(8) programs are vulnerable to remote code execution.
- The flaw allows command injection due to unvalidated domain search list options in IPv6 router advertisements.
- Unquoted input is passed directly to the resolvconf(8) shell script, enabling arbitrary command execution.
- Attackers can leverage this vulnerability from the same network segment.
- The vulnerability does not cross network boundaries, as router advertisements are not routable.
- Systems not using IPv6 or not configured to accept router advertisement messages are not affected.
- Immediate patching or system upgrade to corrected FreeBSD versions is essential.
Timeline
- 2025-12-16 — FreeBSD-SA-25:12.rtsold Security Advisory Announced
- 2025-12-16 — Correction issued for FreeBSD 15.0-STABLE / 15.0-RELEASE-p1
- 2025-12-16 — Correction issued for FreeBSD 14.3-STABLE / 14.3-RELEASE-p7
- 2025-12-16 — Correction issued for FreeBSD 13.4-STABLE / 13.5-RELEASE-p8
Why This Matters
This vulnerability highlights the critical importance of robust input validation in network-facing services. While the attack is limited to the local network segment, successful exploitation of remote code execution can lead to complete system compromise, data breaches, and service disruption. Organizations must prioritize immediate patching to prevent potential attacks and ensure the integrity of their IPv6 infrastructure.